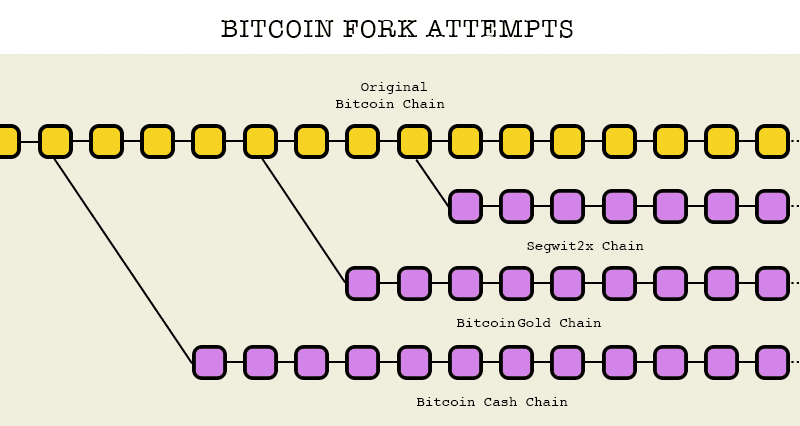
2017 is turning out to be the year of the airdropped Bitcoin fork. First Bitcoin Cash, then Bitcoin Gold, then SegWit2X. Now the ecosystem…
Securing Your Financial Sovereignty
2017 is turning out to be the year of the airdropped Bitcoin fork. First Bitcoin Cash, then Bitcoin Gold, then SegWit2X. Now the ecosystem is primed to become even more confusing, as multiple forks vy for the title of “the real Bitcoin.”
What is “the real Bitcoin?” I’m not sure it’s possible to objectively define it based upon metrics collected at a given snapshot in time. Rather, the only thing that you can be assured of is what the “real Bitcoin” is from your own perspective — the rules to which you agree and which you enforce. Note that this article applies to every single Bitcoin fork: past, present, and future.
Full Nodes For Freedom
How do you enforce the rules to which you agree? You have to run a fully validating Bitcoin node and actually use it to verify payments you receive. Nodes act as your personal sentinel, protecting you against fraudulent activity. They reject actions undertaken by rule breakers, even while you’re busy or asleep.
Full nodes offer the best privacy model. If you’re using a centralized wallet, you have no privacy — the wallet provider knows all of your transactions and addresses. If you’re using an SPV wallet, your privacy is not obviously as terrible, but is nonetheless fundamentally broken. With a full node, you download all the blockchain data and only query for addresses / transactions locally — network observers can’t see what you’re interested in.
Full nodes offer the strongest security model. If you’re using a centralized wallet, you’re completely trusting that they are running nodes that enforce the rules of the network. If you’re using an SPV wallet, you’re trusting that the majority of hashpower is validating the rules of the network to which you agree.
If you configure your node to accept incoming connections, it helps the network by sending blocks and transactions to other full nodes to help them sync, and it services data requests from lightweight wallets. From this standpoint full nodes altruistically support the health of the network.
From a macro perspective, full nodes keep the network honest. The more entities who are actively running nodes to audit their economic interactions, the more robust the network is against attacks. If you’re thinking from a nation-state attack scenario, more nodes = more “doors that have to be kicked down” in order to coerce the node owner into making changes against their will.
Source/More: Securing Your Financial Sovereignty – Jameson Lopp – Medium