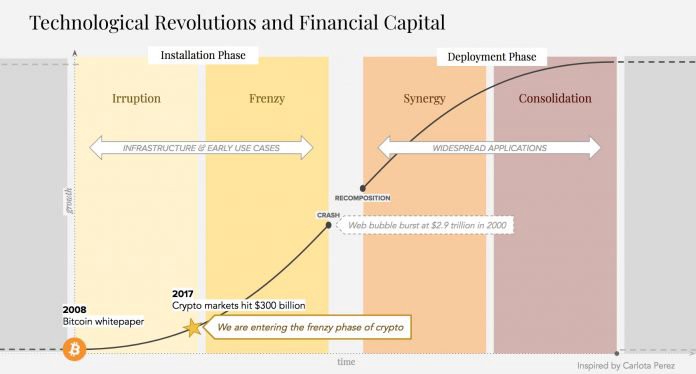
Extorting bitcoin using ransomware is a profitable business. One Google report pegged a group of extortionists making $25 million in two years. Now, at least one Tor proxy service is trying to get its cut, as it was caught diverting victims’ payments to its own wallets.
Ransomware extortionists ask their victims to pay in bitcoin, and to use the deep web so they can escape authorities. When a ransomware victim doesn’t want to or isn’t able to install the Tor browser, used to access the deep web’s .onion domains, operators ask them to use a Tor proxy, such as onion.top or onion.to.
Tor proxy services allow users to access .onion websitse using a regular browser such as Google Chrome, Edge, or Firefox, simply by adding the .top or .to extension to the end of any Tor URL. These services have been getting increasingly popular among ransomware authors. So much so, a few strains even added alternative URLs to help victims pay using these services.
According to cybersecurity firm Proofpoint, at least one of these services, onion.top, was caught replacing the ransomware’s bitcoin payment address with its own. Per the researchers, the service was secretly doing this, and has seemingly netted over $22,000 from the move.
Researchers discovered onion.top was doing this after noticing a ransomware strain dubbed LockeR warned users not to use the service as it was stealing its bitcoin. The warning reads:
“Do NOT use onion.top, they are replacing the bitcoin address with their own and stealing bitcoins. To be sure you’re paying to the correct address, use Tor Browser.”
Source/More: Tor Proxy Service Caught Diverting Ransomware Extortionists’ Bitcoin Payments