Inspired by 2-part series 6 Solidity Vulnerabilities and How to Stop Them, I thought I’d write a bit about some of the more nuanced vulnerabilities that are related to mechanism design. In simple words, we will go over the vulnerabilities that arise from how smart contracts can interact with each other beyond what the author intended with the initial code.
For now, I’ll cover 2 main categories: Frontrunning and Malicious Smart Contract Wrapping. In a future article, I will go expand on some more complex game theory based flaws. Let’s begin!
Frontrunning
Frontrunning is a term from the trading world, where if another trader can see you are making a large order before it hits the exchange (let’s say, a large BUY order), they can put a smaller BUY “in front” of yours, and benefit from your order’s movement of the market. They will sell right after your order executes, therefore having made some “risk-free” profit at your expense.
In Ethereum, this is relevant as well for trading, but it has implications outside of that due to the transparent nature of the P2P network. Let’s look at this contract as an example:
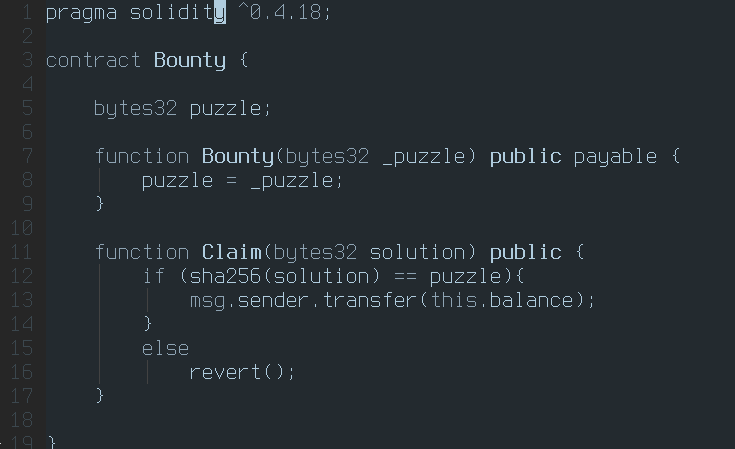
The contract is fairly simple. The constructor sets a hash value and an amount of ETH, and sets that as the challenge for the prize. Anyone who can figure out what hashes to puzzle can claim the prize. There is nothing wrong in the solidity code per se, it is just naively programmed.
The same way that an adversarial trader can frontrun your trade, so can an adversarial network user “ftontrun” your solution here. If the adversary is aware of this contract (perhaps the prize for this solution is in the millions, and hence many are watching it), they can scan the network and check when someone submits a valid solution. Once they see this tx in the mempool, they can take the solution, and resubmit it with their own address with a higher gas price, and if they manage to get their tx in before you, they’ll have stolen your prize!
Of course, another scenario is the miners themselves stealing your prize. In that case, they don’t even have to play the gas price game, they can simply choose not to include your tx in their block, and place their own in with the solution.
Source/More: Mechanism Design Security in Smart Contracts – Matthew Di Ferrante – Medium